




Advanced cybersecurity services to protect digital assets from evolving threats.






Every project we undertake follows a structured approach, from initial consultation to final delivery and beyond.

Step 1
We begin by deeply understanding your business goals, challenges, and requirements. Our team works closely with you to align our strategy with your vision.

Step 2
Based on our analysis, we develop a comprehensive strategy and detailed project plan that outlines timelines, milestones, and deliverables.

Step 3
We execute the plan with precision, building robust solutions, launching them successfully, and continuously optimizing for peak performance.

Step 4
We ensure smooth delivery and provide ongoing support, maintenance, and updates to keep your solutions running at their best.
Discover our most successful projects showcasing every service we offer. Use the filter buttons above to select a specific service.
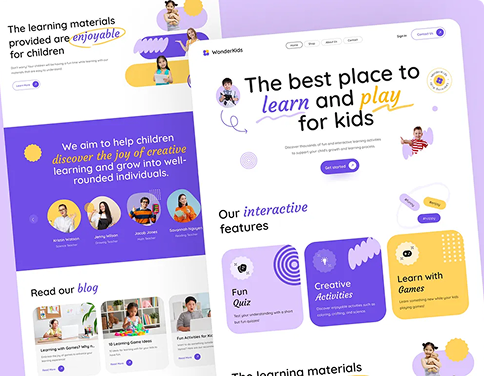
Creative Design
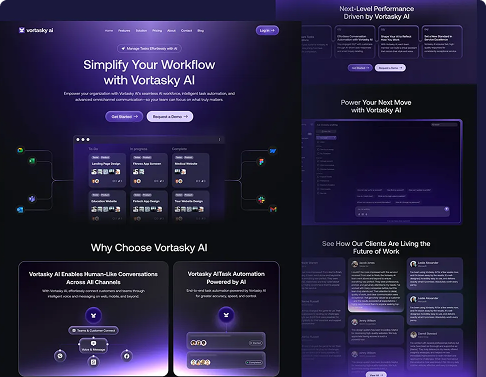
Development
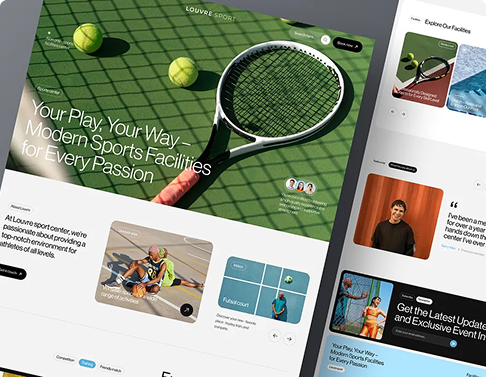
Creative Design
Every business is unique, and so are its challenges. We craft customized design solutions that align perfectly with your goals. Let’s discuss your vision and turn it into a seamless, user-friendly experience.
Let's Talk